 WExploit (computer security)
WExploit (computer security) WVulnerability (computing)
WVulnerability (computing) WArbitrary code execution
WArbitrary code execution WArmitage (computing)
WArmitage (computing) WBlueKeep
WBlueKeep WCode injection
WCode injection WCross-site scripting
WCross-site scripting WCryptojacking malware
WCryptojacking malware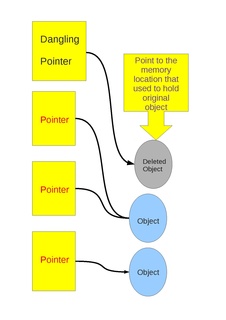 WDangling pointer
WDangling pointer WDirtyTooth
WDirtyTooth WDrive-by download
WDrive-by download WDROWN attack
WDROWN attack WEFAIL
WEFAIL WTor (network)
WTor (network) WEvil maid attack
WEvil maid attack WForeshadow
WForeshadow WHeartbleed
WHeartbleed WIdle scan
WIdle scan WInteger overflow
WInteger overflow WKRACK
WKRACK WLoad value injection
WLoad value injection WMalware
WMalware WMeltdown (security vulnerability)
WMeltdown (security vulnerability) WMetasploit Project
WMetasploit Project WMicroarchitectural Data Sampling
WMicroarchitectural Data Sampling WPayload (computing)
WPayload (computing) WPrivilege escalation
WPrivilege escalation WRace condition
WRace condition WReflected DOM Injection
WReflected DOM Injection WRyuk (ransomware)
WRyuk (ransomware) WShellcode
WShellcode WSmudge attack
WSmudge attack WSpectre (security vulnerability)
WSpectre (security vulnerability) WSQL injection
WSQL injection WStagefright (bug)
WStagefright (bug) WSwatting
WSwatting WTimeline of computer viruses and worms
WTimeline of computer viruses and worms WVault 7
WVault 7 WComputer virus
WComputer virus WWannaCry ransomware attack
WWannaCry ransomware attack WWarchalking
WWarchalking WWardriving
WWardriving W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W