 W
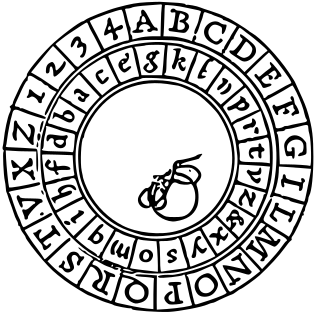
WThe Alberti Cipher, created in 1467 by Italian architect Leon Battista Alberti, was one of the first polyalphabetic ciphers. In the opening pages of his treatise De componendis cifris he explained how his conversation with the papal secretary Leonardo Dati about a recently developed movable type printing press led to the development of his cipher wheel.
 W
WThe ARPANET pioneered the creation of novel encryption devices for packet networks in the 1970s and 1980s, and as such were ancestors to today's IPsec architecture, and High Assurance Internet Protocol Encryptor (HAIPE) devices more specifically.
 W
WThe BID 770 was a British-built electronic cryptography device, codenamed TOPIC. It was also used by Canada's foreign service under the codename TENEC. TOPIC was brought into service in 1977, and became obsolete in 1995.
 W
WThe C-35 and C-36 were cipher machines designed by Swedish cryptographer Boris Hagelin in the 1930s. These were the first of Hagelin's cipher machines to feature the pin-and-lug mechanism. A later machine in the same series, the C-38, was designated CSP-1500 by the United States Navy and M-209 by the United States military, who used it extensively.
 W
WThe (Hagelin) C-52 and CX-52 were cipher machines manufactured by Crypto AG starting 1951/1952. These pin-and-lug type cipher machines were advanced successors of the C-38/M-209. The machine measures 8+1⁄2 by 5+3⁄8 by 4+3⁄8 inches. The device is mechanical, but when combined with an electric keyboard attachment, the B-52, the resultant system is termed the BC-52. The B-52 is larger, measuring 12+1⁄2 by 8+1⁄2 by 6+3⁄8 inches.
 W
WThe (Hagelin) CD-57 was a portable, mechanical cipher machine manufactured by Crypto AG, first produced in 1957. It was derived from the earlier CD-55, and was designed to be compatible with the larger C-52 machines. Compact, the CD-57 measured merely 5 1/8in × 3 1/8in × 1 1/2in and weighed 1.5 pounds. The CD-57 used six wheels.
 W
WA cipher disk is an enciphering and deciphering tool developed in 1470 by the Italian architect and author Leon Battista Alberti. He constructed a device, consisting of two concentric circular plates mounted one on top of the other. The larger plate is called the "stationary" and the smaller one the "moveable" since the smaller one could move on top of the "stationary".
 W
WThe Combined Cipher Machine (CCM) was a common cipher machine system for securing Allied communications during World War II and, for a few years after, by NATO. The British Typex machine and the US ECM Mark II were both modified so that they were interoperable.
 W
WCommunications security is the discipline of preventing unauthorized interceptors from accessing telecommunications in an intelligible form, while still delivering content to the intended recipients.
 W
WThe TgS-1 DUDEK was an on-line and off-line encryption system developed during the Cold War in the 1960s in the Polish People's Republic by the Telkom Teletra company and the Ministry of Interior for use on teleprinter circuits. The units saw use in the Polish Ministerstwo Spraw Wewnętrznych networks serving the, the, the Polish Ministry of National Defense, the Ministry of Foreign Affairs and the National Bank of Poland. The Poles also pressed Warsaw Pact states to adopt the DUDEK sets for international traffic.
 W
WAn Encrypting PIN Pad is an apparatus for encrypting an identifier such as a PIN entered on a keypad. These are used in Automated teller machines to ensure that the unencrypted PIN is not stored or transmitted anywhere in the rest of the system and thus cannot be revealed accidentally or through manipulations of the system.
 W
WThe Enigma machine is a cipher device developed and used in the early- to mid-20th century to protect commercial, diplomatic, and military communication. It was employed extensively by Nazi Germany during World War II, in all branches of the German military. The Germans believed, erroneously, that use of the Enigma machine enabled them to communicate securely and thus enjoy a huge advantage in World War II. The Enigma machine was considered so secure that it was used to encipher even the most top-secret messages.
 W
WFish was the UK's GC&CS Bletchley Park codename for any of several German teleprinter stream ciphers used during World War II. Enciphered teleprinter traffic was used between German High Command and Army Group commanders in the field, so its intelligence value (Ultra) was of the highest strategic value to the Allies. This traffic normally passed over landlines, but as German forces extended their geographic reach beyond western Europe, they had to resort to wireless transmission.
 W
WThe HC-9 was a mechanical cipher device manufactured by Swedish company AB Transvertex. The HC-9 was designed after World War II and was made in the early 1950s, likely remained in use up to the 1970s. The machine was used for low-level communications. The machine is 18 x 15 x 7 cm.
 W
WJADE was the codename given by US codebreakers to a Japanese World War II cipher machine. The Imperial Japanese Navy used the machine for communications from late 1942 until 1944. JADE was similar to another cipher machine, CORAL, with the main difference that JADE was used to encipher messages in katakana using an alphabet of 50 symbols.
 W
WThe Jefferson disk, or wheel cypher as Thomas Jefferson named it, also known as the Bazeries Cylinder, is a cipher system using a set of wheels or disks, each with the 26 letters of the alphabet arranged around their edge. The order of the letters is different for each disk and is usually scrambled in some random way. Each disk is marked with a unique number. A hole in the centre of the disks allows them to be stacked on an axle. The disks are removable and can be mounted on the axle in any order desired. The order of the disks is the cipher key, and both sender and receiver must arrange the disks in the same predefined order. Jefferson's device had 36 disks. [Kahn, p. 194]
 W
WIn the history of cryptography, the Kryha machine was a device for encryption and decryption, appearing in the early 1920s and used until the 1950s. The machine was the invention of Alexander von Kryha. During the Second World War, Kryha worked as an officer for the German Wehrmacht. There were several versions; the standard Kryha machine weighed around five kilograms, and was totally mechanical. A scaled down pocket version was introduced later on, termed the "Lilliput" model. There was also a more bulky electrical version.
 W
WThe Lorenz SZ40, SZ42a and SZ42b were German rotor stream cipher machines used by the German Army during World War II. They were developed by C. Lorenz AG in Berlin. The model name SZ was derived from Schlüssel-Zusatz, meaning cipher attachment. The instruments implemented a Vernam stream cipher.
 W
WThe M-94 was a piece of cryptographic equipment used by the United States Army, consisting of several lettered discs arranged as a cylinder. It was also employed by the US Navy, under the name CSP 488.
 W
WIn cryptography, the M-209, designated CSP-1500 by the United States Navy is a portable, mechanical cipher machine used by the US military primarily in World War II, though it remained in active use through the Korean War. The M-209 was designed by Swedish cryptographer Boris Hagelin in response to a request for such a portable cipher machine, and was an improvement of an earlier machine, the C-36.
 W
WA PIN pad or PIN entry device (PED) is an electronic device used in a debit, credit or smart card-based transaction to accept and encrypt the cardholder's personal identification number (PIN).
 W
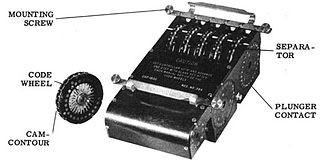
WIn cryptography, a pinwheel was a device for producing a short pseudorandom sequence of bits, as a component in a cipher machine. A pinwheel consisted of a rotating wheel with a certain number of positions on its periphery. Each position had a "pin", "cam" or "lug" which could be either "set" or "unset". As the wheel rotated, each of these pins would in turn affect other parts of the machine, producing a series of "on" or "off" pulses which would repeat after one full rotation of the wheel. If the machine contained more than one wheel, usually their periods would be relatively prime to maximize the combined period. Pinwheels might be turned through a purely mechanical action or electromechanically.
 W
WIn the history of cryptography, the "System 97 Typewriter for European Characters" (九七式欧文印字機) or "Type B Cipher Machine", codenamed Purple by the United States, was an encryption machine used by the Japanese Foreign Office from February 1939 to the end of World War II. The machine was an electromechanical device that used stepping-switches to encrypt the most sensitive diplomatic traffic. All messages were written in the 26-letter English alphabet, which was commonly used for telegraphy. Any Japanese text had to be transliterated or coded. The 26-letters were separated using a plug board into two groups, of six and twenty letters respectively. The letters in the sixes group were scrambled using a 6 × 25 substitution table, while letters in the twenties group were more thoroughly scrambled using three successive 20 × 25 substitution tables.
 W
WRockex, or Telekrypton, was an offline one-time tape Vernam cipher machine known to have been used by Britain and Canada from 1943. It was developed by Canadian electrical engineer Benjamin deForest Bayly, working during the war for British Security Coordination.
 W
WThe Schlüsselgerät 41, also known as the SG-41 or Hitler mill, was a rotor cipher machine, first produced in 1941 in Nazi Germany, that was designed as a potential successor for the Enigma machine. It saw limited use by the Abwehr towards the end of World War II.
 W
WIn cryptography, a scytale is a tool used to perform a transposition cipher, consisting of a cylinder with a strip of parchment wound around it on which is written a message. The ancient Greeks, and the Spartans in particular, are said to have used this cipher to communicate during military campaigns.
 W
WA secret decoder ring is a device which allows one to decode a simple substitution cipher - or to encrypt a message by working in the opposite direction.
 W
WSectéra is a family of secure voice and data communications products made by General Dynamics Mission Systems which are approved by the United States National Security Agency. Devices in the family can use either the National Institute of Standards and Technology (NIST) Advanced Encryption Standard (AES) or SCIP to provide Type 1 encryption, with communication levels classified up to Top Secret. The devices are activated with a Personal Identification Number (PIN).
A secure access module or secure application module (SAM) is a piece of cryptographic hardware typically used by smart card card readers to perform mutual key authentication. SAMs can be used to manage access in a variety of contexts, such as public transport fare collection and point of sale devices.
 W
WSecure Terminal Equipment (STE) is the U.S. government's current, encrypted telephone communications system for wired or "landline" communications. STE is designed to use ISDN telephone lines which offer higher speeds of up to 128 kbit/s and are all digital. The greater bandwidth allows higher quality voice and can also be utilized for data and fax transmission through a built-in RS-232 port. STE is intended to replace the older STU-III office system and the KY-68 tactical system. STE sets are backwards compatible with STU-III phones, but not with KY-68 sets.
 W
WThe Siemens & Halske T52, also known as the Geheimschreiber, or Schlüsselfernschreibmaschine (SFM), was a World War II German cipher machine and teleprinter produced by the electrical engineering firm Siemens & Halske. The instrument and its traffic were codenamed Sturgeon by British cryptanalysts.
 W
WIn the history of cryptography, the ECM Mark II was a cipher machine used by the United States for message encryption from World War II until the 1950s. The machine was also known as the SIGABA or Converter M-134 by the Army, or CSP-888/889 by the Navy, and a modified Navy version was termed the CSP-2900.
 W
WSIGCUM, also known as Converter M-228, was a rotor cipher machine used to encrypt teleprinter traffic by the United States Army. Hastily designed by William Friedman and Frank Rowlett, the system was put into service in January 1943 before any rigorous analysis of its security had taken place. SIGCUM was subsequently discovered to be insecure by Rowlett, and was immediately withdrawn from service. The machine was redesigned to improve its security, reintroduced into service by April 1943, and remained in use until the 1960s.
 W
WSIGSALY was a secure speech system used in World War II for the highest-level Allied communications. It pioneered a number of digital communications concepts, including the first transmission of speech using pulse-code modulation.
 W
WSIGTOT was a one-time tape machine for encrypting teleprinter communication that was used by the United States during World War II and after for the most sensitive message traffic. It was developed after security flaws were discover in an earlier rotor machine for the same purpose, called SIGCUM. SIGTOT was designed by Leo Rosen and used the same Bell Telephone 132B2 mixer as SIGCUM. The British developed a similar machine called the 5-UCO. Later an improved mixer, the SSM-33, replaced the 131B2,
 W
WIn the history of cryptography, 91-shiki ōbun injiki or Angōki Taipu-A , codenamed Red by the United States, was a diplomatic cryptographic machine used by the Japanese Foreign Office before and during World War II. A relatively simple device, it was quickly broken by western cryptographers. The Red cipher was succeeded by the Type B "Purple" machine which used some of the same principles. Parallel usage of the two systems assisted in the breaking of the Purple system.