 W
WAnycast is a network addressing and routing methodology in which a single destination IP address is shared by devices in multiple locations. Routers direct packets addressed to this destination to the location nearest the sender, using their normal decision-making algorithms, typically the lowest number of BGP network hops. Anycast routing is widely used by content delivery networks such as web and DNS hosts, to bring their content closer to end users.
 W
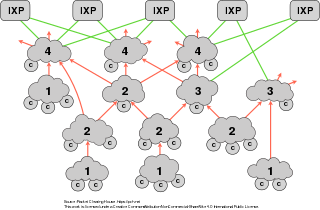
WThe Internet backbone may be defined by the principal data routes between large, strategically interconnected computer networks and core routers of the Internet. These data routes are hosted by commercial, government, academic and other high-capacity network centers, as well as the Internet exchange points and network access points, that exchange Internet traffic between the countries, continents, and across the oceans. Internet service providers, often Tier 1 networks, participate in Internet backbone traffic by privately negotiated interconnection agreements, primarily governed by the principle of settlement-free peering.
 W
WA butterfly network is a technique to link multiple computers into a high-speed network. This form of multistage interconnection network topology can be used to connect different nodes in a multiprocessor system. The interconnect network for a shared memory multiprocessor system must have low latency and high bandwidth unlike other network systems, like local area networks (LANs) or internet for three reasons:Messages are relatively short as most messages are coherence protocol requests and responses without data.Messages are generated frequently because each read-miss or write-miss generates messages to every node in the system to ensure coherence. Read/write misses occur when the requested data is not in the processor's cache and must be fetched either from memory or from another processor's cache.Messages are generated frequently, therefore rendering it difficult for the processors to hide the communication delay.
 W
WA classful network is a network addressing architecture used in the Internet from 1981 until the introduction of Classless Inter-Domain Routing in 1993. The method divides the IP address space for Internet Protocol version 4 (IPv4) into five address classes based on the leading four address bits. Classes A, B, and C provide unicast addresses for networks of three different network sizes. Class D is for multicast networking and the class E address range is reserved for future or experimental purposes.
 W
WA core router is a router designed to operate in the Internet backbone, or core. To fulfill this role, a router must be able to support multiple telecommunications interfaces of the highest speed in use in the core Internet and must be able to forward IP packets at full speed on all of them. It must also support the routing protocols being used in the core. A core router is distinct from an edge router: edge routers sit at the edge of a backbone network and connect to core routers.
 W
WEcho is a group communications protocol where authenticated and encrypted information is addressed to members connected to a node.
 W
WFuture Internet testbeds / experimentation between BRazil and Europe (FIBRE) is a research project co-funded by the Conselho Nacional de Desenvolvimento Científico e Tecnológico of Brazil and the European Commission under the seventh of the Framework Programmes for Research and Technological Development (FP7).
 W
WIn routing, the forwarding plane, sometimes called the data plane or user plane, defines the part of the router architecture that decides what to do with packets arriving on an inbound interface. Most commonly, it refers to a table in which the router looks up the destination address of the incoming packet and retrieves the information necessary to determine the path from the receiving element, through the internal forwarding fabric of the router, and to the proper outgoing interface(s).
 W
WFuture Internet Research and Experimentation (FIRE) is a program funded by the European Union to do research on the Internet, its prospects, and its future, a field known as "future Internet".
 W
WThe Internet Mapping Project was started by William Cheswick and Hal Burch at Bell Labs in 1997. It has collected and preserved traceroute-style paths to some hundreds of thousands of networks almost daily since 1998. The project included visualization of the Internet data, and the Internet maps were widely disseminated.
 W
WInternet transit is the service of allowing network traffic to cross or "transit" a computer network, usually used to connect a smaller Internet service provider (ISP) to the larger Internet. Technically, it consists of two bundled services:The advertisement of customer routes to other ISPs, thereby soliciting inbound traffic toward the customer from them The advertisement of other ISPs' routes to the ISP's customer, thereby soliciting outbound traffic from the customer towards these networks.
 W
WIn computer networking, IP over Avian Carriers (IPoAC) is a proposal to carry Internet Protocol (IP) traffic by birds such as homing pigeons. IP over Avian Carriers was initially described in RFC 1149, a Request for Comments (RFC) issued by the Internet Engineering Task Force (IETF), written by D. Waitzman, and released on April 1, 1990. It is one of several April Fools' Day Request for Comments.
 W
WIPv4 address exhaustion is the depletion of the pool of unallocated IPv4 addresses. Because the original Internet architecture had fewer than 4.3 billion addresses available, depletion has been anticipated since the late 1980s, when the Internet started experiencing dramatic growth. This depletion is one of the reasons for the development and deployment of its successor protocol, IPv6. IPv4 and IPv6 coexist on the Internet.
 W
WMaltego is software used for open-source intelligence and forensics, developed by Paterva from Pretoria, South Africa. Maltego focuses on providing a library of transforms for discovery of data from open sources, and visualizing that information in a graph format, suitable for link analysis and data mining. As of 2019, the team of Maltego Technologies headquartered in Munich, Germany has taken responsibility for all global customer-facing operations.
 W
WMbone was an experimental backbone and virtual network built on top of the Internet for carrying IP multicast traffic on the Internet. It was developed in the early 1990s and required specialized hardware and software. Since the operators of most Internet routers have disabled IP multicast due to concerns regarding bandwidth tracking and billing, the Mbone was created to connect multicast-capable networks over the existing Internet infrastructure.
 W
WIn computer networking, multicast is group communication where data transmission is addressed to a group of destination computers simultaneously. Multicast can be one-to-many or many-to-many distribution. Multicast should not be confused with physical layer point-to-multipoint communication.
 W
WMulticast Routing is one of the routing protocols in TCP/IP communication.
 W
WnetTransformer is a cross-platform, network discovery program. The software has been created with the idea of discovering through a set of SNMP queries IP networks state to produce various data models from and then to use the data from the models and other inputs to transform the network from one "state" to another. As per the original PhD the author has used netTransformer to demonstrate a network transformation of an ISP network from IPv4 to an IPv6 state. The transformation is a long lasting process typically driven by a strategy that passes through many states. For example, the initial state is the current state in which the network and the services offered by it are IPv4 only. The long term goal is a network and service that is IPv6 only. To achieve it the ISP will has to pass through many intermediate states depending of its transformation strategy.
 W
WNetwork mapping is the study of the physical connectivity of networks e.g. the Internet. Network mapping discovers the devices on the network and their connectivity. It is not to be confused with network discovery or network enumerating which discovers devices on the network and their characteristics such as. The field of automated network mapping has taken on greater importance as networks become more dynamic and complex in nature.
 W
WNJFX, also known as New Jersey Fiber Exchange, is a Wall Township, NJ-based data center and subsea cable landing station operator. The company offers Tier 3 data center, meet-me room and colocation services, and a cable landing station on a 58 acre campus.
 W
WThe Opte Project, created in 2003 by Barrett Lyon, seeks to generate an accurate representation of the breadth of the Internet using visual graphics. Lyon believes that his network mapping can help teach students more about the Internet while also acting as a gauge illustrating both overall Internet growth and the specific areas where that growth occurs. It was not the first such project; others predated it, such as the Bell Labs Internet Mapping Project.
 W
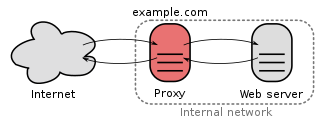
WIn computer networking, a proxy server is a server application that acts as an intermediary between a client requesting a resource and the server providing that resource.
 W
WIn computer networks, a reverse proxy is a type of proxy server that retrieves resources on behalf of a client from one or more servers. These resources are then returned to the client, appearing as if they originated from the reverse proxy server itself. It is mainly used to balance load.
 W
WA router is a networking device that forwards data packets between computer networks. Routers perform the traffic directing functions on the Internet. Data sent through the internet, such as a web page or email, is in the form of data packets. A packet is typically forwarded from one router to another router through the networks that constitute an internetwork until it reaches its destination node.
 W
WSorcerer's Apprentice Syndrome (SAS) is a network protocol flaw in the original versions of TFTP. It was named after Goethe's 1797 poem "Der Zauberlehrling", because the details of its operation closely resemble the disaster that befalls the sorcerer's apprentice: the problem resulted in an ever-growing replication of every packet in the transfer.
 W
WA subnetwork or subnet is a logical subdivision of an IP network. The practice of dividing a network into two or more networks is called subnetting.
 W
WA supernetwork, or supernet, is an Internet Protocol (IP) network that is formed by combination of multiple networks into a larger network. The new routing prefix for the combined network represents the constituent networks in a single routing table entry. The process of forming a supernet is called supernetting, prefix aggregation, route aggregation, or route summarization.
 W
WA Tier 1 network is an Internet Protocol (IP) network that can reach every other network on the Internet solely via settlement-free interconnection. Tier 1 networks can exchange traffic with other Tier 1 networks without paying any fees for the exchange of traffic in either direction. In contrast, some Tier 2 networks and all Tier 3 networks must pay to transmit traffic on other networks.
 W
WA Tier 2 network is an Internet service provider which engages in the practice of peering with other networks, but which also purchases IP transit to reach some portion of the Internet.
 W
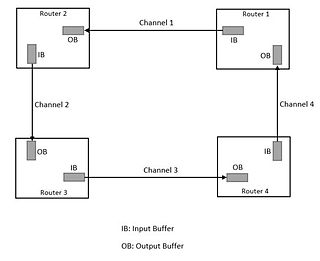
WA routing algorithm decides the path followed by a packet from the source to destination routers in a network. An important aspect to be considered while designing a routing algorithm is avoiding a deadlock. Turn restriction routing is a routing algorithm for mesh-family of topologies which avoids deadlocks by restricting the types of turns that are allowed in the algorithm while determining the route from source node to destination node in a network.
 W
WIn computer networking, unicast is a one-to-one transmission from one point in the network to another point; that is, one sender and one receiver, each identified by a network address.
 W
WHerbert Van de Sompel is a Belgian librarian, computer scientist, and musician, most known for his role in the development of the Open Archives Initiative (OAI) and standards such as OpenURL, Object Reuse and Exchange, and the OAI Protocol for Metadata Harvesting.
 W
WThe explicit multi-unicast (Xcast) is a variation of multicast that supports a great number of multicast sessions with a small number of recipients in each. It adds all the destination IP addresses in the IP header, instead of using a multicast address. The traditional multicast schemes over Internet Protocol (IP) scale to multicast groups with many members, but they have scalability problems for a great number of groups. Multicast schemes can be used to minimize the bandwidth consumption. Xcast minimizes bandwidth consumption for small groups, by eliminating the signaling protocols and state information for every session of the standard IP multicast scheme.