 W
WMalware is any software intentionally designed to cause damage to a computer, server, client, or computer network. By contrast, software that causes unintentional harm due to some deficiency is typically described as a software bug. A wide variety of malware types exist, including computer viruses, worms, Trojan horses, ransomware, spyware, adware, rogue software, wiper and scareware.
 W
WBlaster was a computer worm that spread on computers running operating systems Windows XP and Windows 2000 during August 2003.
 W
WBlue Frog was a freely-licensed anti-spam tool produced by Blue Security Inc. and operated as part of a community-based system which tried to persuade spammers to remove community members' addresses from their mailing lists by automating the complaint process for each user as spam is received. Blue Security maintained these addresses in a hashed form in a Do Not Intrude Registry, and spammers could use free tools to clean their lists. The tool was discontinued in 2006.
 W
WA botnet is a number of Internet-connected devices, each of which is running one or more bots. Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allow the attacker to access the device and its connection. The owner can control the botnet using command and control (C&C) software. The word "botnet" is a portmanteau of the words "robot" and "network". The term is usually used with a negative or malicious connotation.
 W
WThe Cascade virus is a prominent computer virus that was a resident written in assembly language, that was widespread in the 1980s and early 1990s. It infected .COM files and had the effect of making text on the screen fall down and form a heap at the bottom of the screen. It was notable for using an encryption algorithm to avoid being detected. However, one could see that infected files had their size increased by 1701 or 1704 bytes. In response, IBM developed its own antivirus software.
 W
WCDex is a free software package for Digital Audio Extraction from Audio CD and audio format conversion for Microsoft Windows. It converts CDDA tracks from a CD to standard computer sound files, such as WAV, MP3, or Ogg Vorbis. CDex was previously released as free software under the terms of the GNU General Public License (GPL); however, although the website claims that this is still the case, no source code has been released since 2005. It was originally written by Albert L. Faber, and is developed and maintained by Georgy Berdyshev. Recent versions of the software may be compromised and a security threat.
 W
WComputer security, cybersecurity or information technology security is the protection of computer systems and networks from information disclosure, theft of or damage to their hardware, software, or electronic data, as well as from the disruption or misdirection of the services they provide.
 W
WThe 2016 Dyn cyberattack was a series of distributed denial-of-service attacks on October 21, 2016, targeting systems operated by Domain Name System (DNS) provider Dyn. The attack caused major Internet platforms and services to be unavailable to large swathes of users in Europe and North America. The groups Anonymous and New World Hackers claimed responsibility for the attack, but scant evidence was provided.
 W
WEvercookie is a JavaScript application programming interface (API) that identifies and reproduces intentionally deleted cookies on the clients' browser storage. It was created by Samy Kamkar in 2010 to demonstrate the possible infiltration from the websites that use respawning. Websites that have adopted this mechanism can identify users even if they attempt to delete the previously stored cookies.
 W
WThe social media platform and social networking service Facebook has been affected multiple times over its history by intentionally harmful software. Known as malware, these pose particular challenges both to users of the platform as well as to the personnel of the tech-company itself. Fighting the entities that create these is a topic of ongoing malware analysis.
 W
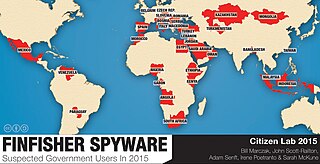
WFinFisher, also known as FinSpy, is surveillance software marketed by Lench IT Solutions plc, which markets the spyware through law enforcement channels.
 W
WGenieo Innovation is an Israeli company, specializing in unwanted software which includes advertising and user tracking software, commonly referred to as a potentially unwanted program, adware, privacy-invasive software, grayware, or malware. They are best known for Genieo, an application of this type. They also own and operate InstallMac which distributes additional 'optional' search modifying software with other applications. In 2014, Genieo Innovation was acquired for $34 million by Somoto, another company which "bundles legitimate applications with offers for additional third party applications that may be unwanted by the user". This sector of the Israeli software industry is frequently referred to as Download Valley.
 W
WHao123 is a Chinese online listings portal by Baidu. It also has a Portuguese and a Thai version.
 W
WLocky is ransomware malware released in 2016. It is delivered by email with an attached Microsoft Word document that contains malicious macros. When the user opens the document, it appears to be full of gibberish, and includes the phrase "Enable macro if data encoding is incorrect," a social engineering technique. If the user does enable macros, they save and run a binary file that downloads the actual encryption Trojan, which will encrypt all files that match particular extensions. Filenames are converted to a unique 16 letter and number combination. Initially, only the .locky file extension was used for these encrypted files. Subsequently, other file extensions have been used, including .zepto, .odin, .aesir, .thor, and .zzzzz. After encryption, a message instructs them to download the Tor browser and visit a specific criminal-operated Web site for further information. The Web site contain instructions that demand a payment of between 0.5 and 1 bitcoin. Since the criminals possess the private key and the remote servers are controlled by them, the victims are motivated to pay to decrypt their files.
 W
WLogicLocker, is a cross-vendor ransomware worm that targets Programmable Logic Controllers (PLCs) used in Industrial Control Systems (ICS). First described in a research paper released by the Georgia Institute of Technology, the malware is capable of hijacking multiple PLCs from various popular vendors. The researchers, using a water treatment plant model, were able to demonstrate the ability to display false readings, shut valves and modify Chlorine release to poisonous levels using a Schneider Modicon M241, Schneider Modicon M221 and an Allen Bradley MicroLogix 1400 PLC. The ransomware is designed to bypass weak authentication mechanisms found in various PLCs and lock out legitimate users while planting a logicbomb into the PLC. As of 14 February 2017, it is noted that there are over 1,400 of the same PLCs used in the proof-of-concept attack that were accessible from the internet as found using Shodan.
 W
WMovieland, also known as Movieland.com, Moviepass.tv and Popcorn.net, was a subscription-based movie download service that has been the subject of thousands of complaints to the Federal Trade Commission, the Washington State Attorney General's Office, the Better Business Bureau, and other agencies by consumers who said they were held hostage by its repeated pop-up windows and demands for payment, triggered after a free 3-day trial period. Many said they had never even heard of Movieland until they saw their first pop-up. Movieland advertised that the service had "no spyware", and that no personal information would need to be filled out to begin the free trial.
 W
WSeculert is a cloud-based cyber security technology company based in Israel. The company’s technology is designed to detect breaches and Advanced Persistent Threats (APTs), attacking networks. Seculert’s business is based on malware research and the ability to uncover malware that has gone undetected by other traditional measures.
 W
WPoint-of-sale malware is usually a type of malicious software (malware) that is used by cybercriminals to target point of sale (POS) and payment terminals with the intent to obtain credit card and debit card information, a card's track 1 or track 2 data and even the CVV code, by various man-in-the-middle attacks, that is the interception of the processing at the retail checkout point of sale system. The simplest, or most evasive, approach is RAM-scraping, accessing the system's memory and exporting the copied information via a remote access trojan (RAT) as this minimizes any software or hardware tampering, potentially leaving no footprints. POS attacks may also include the use of various bits of hardware: dongles, trojan card readers, (wireless) data transmitters and receivers. Being at the gateway of transactions, POS malware enables hackers to process and steal thousands, even millions, of transaction payment data, depending upon the target, the number of devices affected, and how long the attack goes undetected. This is done before or outside of the card information being (usually) encrypted and sent to the payment processor for authorization.
 W
WShamoon, also known as W32.DistTrack, is a modular computer virus that was discovered in 2012, targeting then-recent 32-bit NT kernel versions of Microsoft Windows. The virus was notable due to the destructive nature of the attack and the cost of recovery. Shamoon can spread from an infected machine to other computers on the network. Once a system is infected, the virus continues to compile a list of files from specific locations on the system, upload them to the attacker, and erase them. Finally the virus overwrites the master boot record of the infected computer, making it unusable.
 W
WSpySheriff is malware that disguises itself as anti-spyware software. It attempts to mislead the user with false security alerts, threatening them into buying the program. Like other rogue antiviruses, after producing a list of false threats, it prompts the user to pay to remove them. The software is particularly difficult to remove, since it nests its components in System Restore folders, and also blocks some system management tools. However, SpySheriff can be removed by an experienced user, antivirus software, or by using a rescue disk.
 W
WThis timeline of computer viruses and worms presents a chronological timeline of noteworthy computer viruses, computer worms, Trojan horses, similar malware, related research and events.
 W
WXunlei Limited is a Chinese multinational technology company and an online service provider founded in 2003. The subsidiary of Xunlei Limited, Shenzhen Xunlei Networking Technologies, Co., Ltd. was formerly known as Sandai Technologies (Shenzhen) Inc. and changed its name to Shenzhen Xunlei Networking Technologies, Co., Ltd. in May 2005. Its headquarters are in Nanshan District, Shenzhen.
 W
W W
W